Office 365, Personal OneNote, and URL HTTPS Spearphishing attacks
We adapt, they adapt, we learn, they learn…
The Saga continues…
It’s a Friday night, and here I am dissecting a new Spear phishing attack. However, this one has taken my breath away, since the social engineering aspects of this attack have been exceptionally well done, which makes it very dangerous. And whilst this you may have seen before, it was targetting older people as it was attacking Care Homes.
The email is genuine, and replying to a thread you have already communicated with
It’s a genuine email, it passes SPF, DKIM and DMARC checks, does come from someone that you know, and originates from an Outlook client. They are also replying to a thread you have already communicated with.
The link is also interesting. Normally users check the links in their email, and they do this by us either educating them to hover the mouse over the URL, or by using MIMECAST or another similar tool. Well, if they do - it is a genuine OneDrive link, it is just a personal OneDrive or OneNote page share with no user authentication instead. You then click that link which redirects you to the login screen that is a carbon copy of the Office 365 login, with a Let’s Encrypt certificate and a new URL - where your user has become relaxed and the security tools you have in place (Email scanning, URL scanners) are no longer providing any input.
So the URL is different and not Office 365/Microsoft OneDrive?
Yes, it is. But only on the second click from the users’ perspective. The first one is a genuine OneDrive link in their email from a genuine email with someone you have corresponded too, which looks the same as an Office 365 link. So, from the user’s perspective - they’ve checked the originator, and the email is genuine. They’ve checked the URL, and it is genuine. If you use MIMECAST or a similar service, it passes the checks. They then open the email and they have checked the URL at the top of their browser. They confirm it’s an Office link. They then are embarking on their usual user flow - which is when the user is taken out of the Microsoft ecosystem, as the URL in the OneNote page is to an external service, as it is a carbon copy of the Office 365 login page. If you fill in the details, you are then redirected to another page that has a valid SSL certificate. Which contains the Emotet virus. As Emotet spreads by infecting mailboxes, the vicious cycle continues [1].
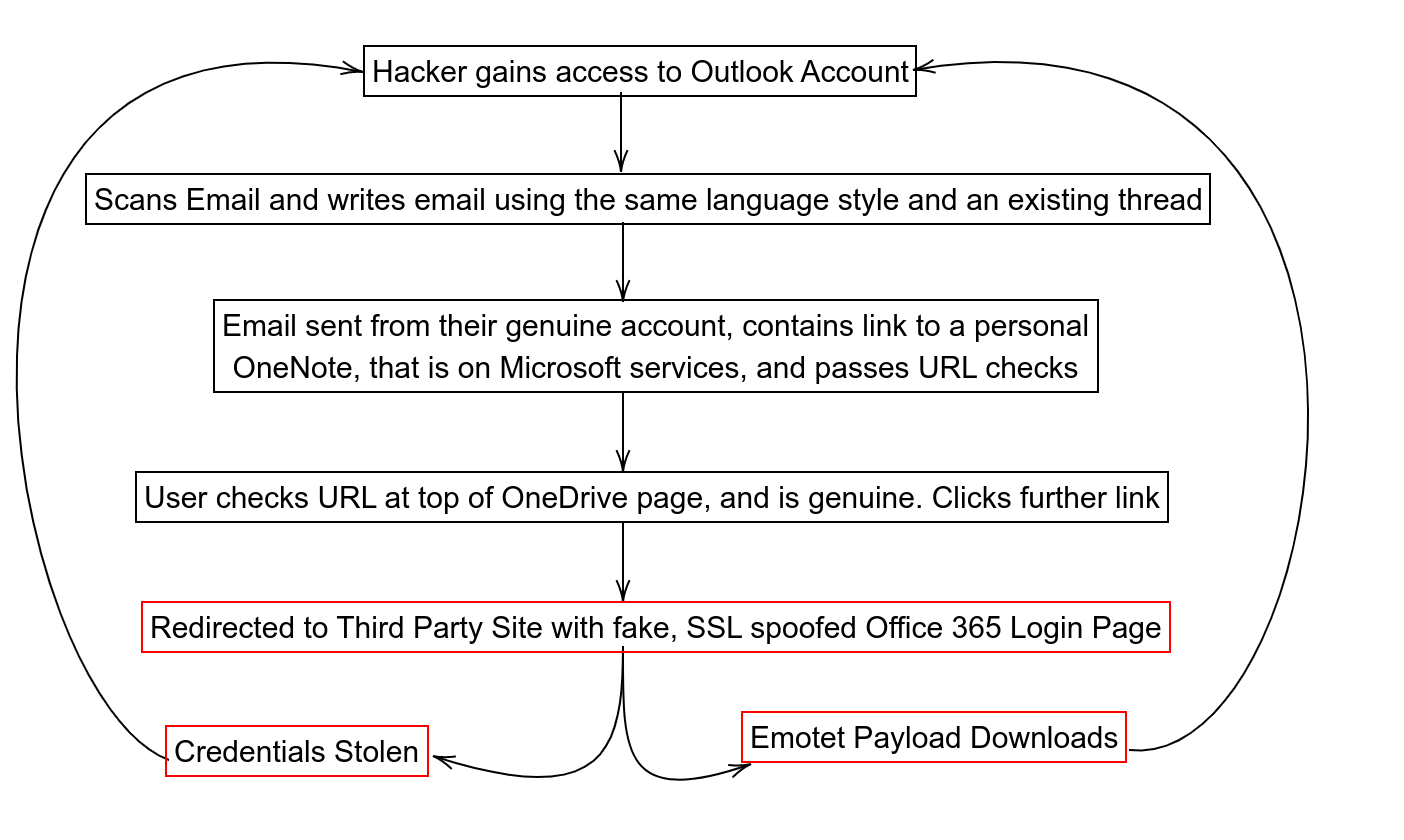
Figure 1.1: User flow of the OneDrive Social Engineering Attack
Each process from this point, however, they have seen SSL certificate green ticks so there are no warning signs for the user, and you have relaxed the user in case they had any worries. If you followed your cybersecurity advice, you most likely would have complied with all of their advice until you got to the exploit, and by then you are already in your safe space.
It also makes abuse reporting procedures harder, as there are multiple places you need to report the violation.
Advice
Remember, in your cybersecurity training, do cover the difference between Phishing and Whaling and Spear Phishing. If you are targeted, and they want you - they will get access. Someone will fall for it. You need to make sure the user can identify when it went wrong, and report it to your security team as soon as possible.
Speed is what is important. The quicker you act, the quicker it stays an event rather than an incident.
Most cybersecurity training only covers things like “email addresses that look like someone you know” or “someone you don’t know”. They can be from someone you DO know, and a genuine email. The URL might be have SSL and be genuine. Until it isn’t.
Remember, as we provide mitigations, they adapt. And never, ever blame the users, because sometimes - it’s your procedures and advice that made them trust the email.
References
[1] What is Emotet